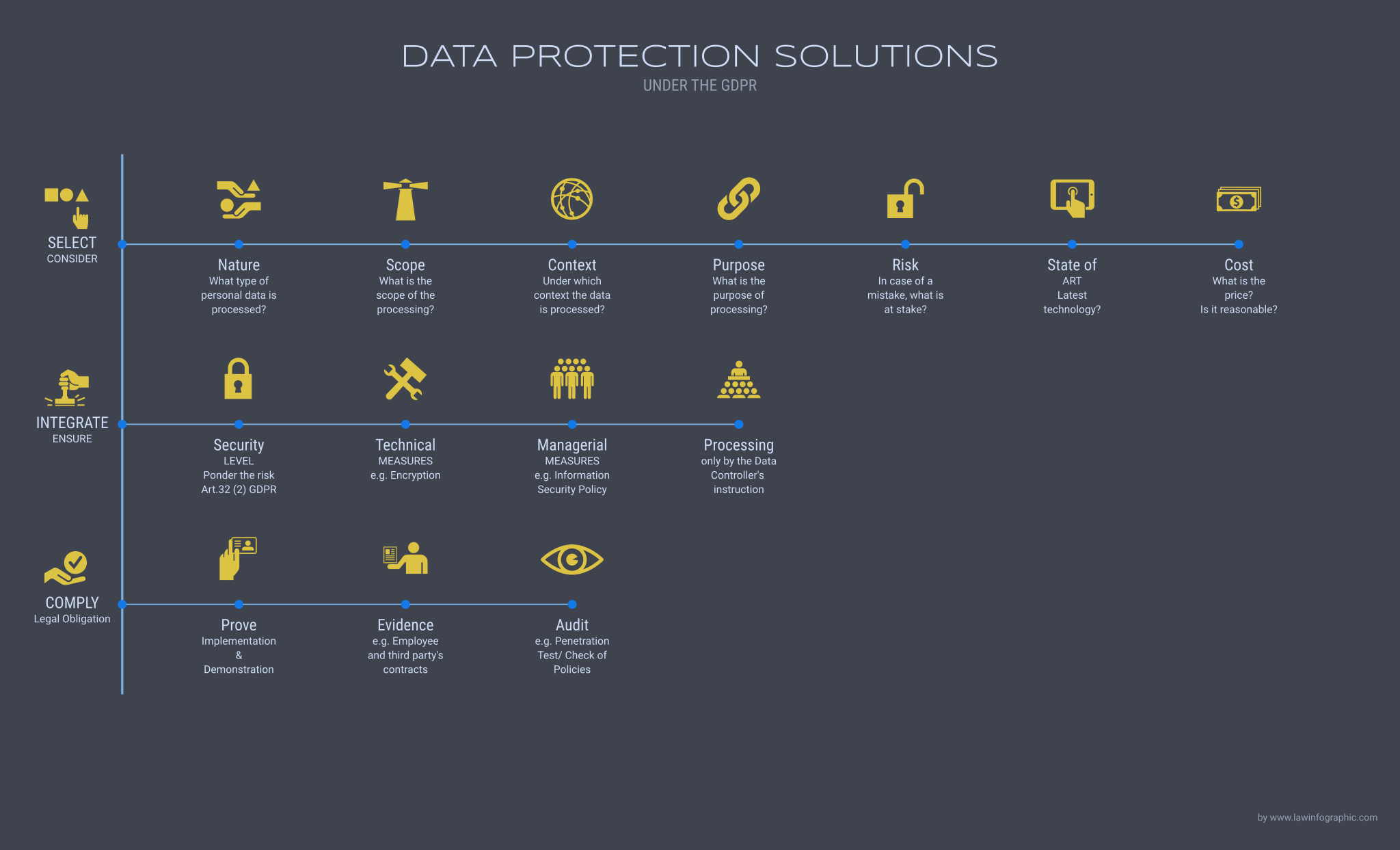
To secure data from internal and external threats, article 32 of the GDPR, provides the following points to be considered in choosing a data protection solution:
Useful? Embed this infographic on your website.
- The state of the art refers to the latest technology available;
- The cost of implementation refers to the price to use such data security. The best solution will not require an unreasonable cost;
- The nature refers to the nature of the personal data to be processed, in particular, whether special categories of personal data are processed;
- The scope refers to the subject matter of the processing;
- The context refers to the specific in which the personal data are processed (factors, conditions, specific industries);
- The purpose of processing refers to the purpose/s for which the personal data is processed (explicit and legitimate and determined at the time of the collection of the personal data); and,
- The risk refers to the harm that might result from improper processing on the data subject’s rights and freedoms.
Furthermore, the GDPR requires that the data protection mechanism chosen ensures the following:
- Level of Security
The level of security that you require will depend on the data you hold, the way you use it and in particular what is at stake if there is a security breach.
- Appropriate Technical and Organisational Measures
In assessing the appropriate level of security, the GDPR asserts that shall be taken into account the risk (as above described) in particular from accidental or unlawful; destruction, loss, alteration, unauthorized disclosure of, or access to personal data transmitted, stored or otherwise processed.
Regarding technical and organisational measures, the GDPR refers to the use, among other things as appropriate of:
o Pseudonymisation, when the data can no longer identify a specific data subject.
o Encryption, encoding data.
o The ability to ensure the confidentiality, integrity, availability, and resilience of processing personal data systems and services, incorporation of data protection principles in systems and services.
o the ability to restore the availability of and access to data in the event of an incident, consolidation of a culture of security and awareness of personal data.
o Regular tests of the effectiveness of security measures, with the aim to avoid the use of outdated or inefficient measures.
The above is not intended to preclude any other measures of data protection.
- Under the Data Controller’s instruction
The GDPR requires that the process of the personal data must be in line with the instructions provided by the controller unless required otherwise by the Union or Member State Law.
In that sense, the Data Processor must provide sufficient guarantees about its security measures to protect the personal data as instructed by the Data Controller. A written contract is necessary for a clear allocation of responsibilities, purpose, means, etc.
- Demonstrate Compliance
In order to establish effective protection, the GDPR has established powers for monitoring, request to demonstrate compliance and set of sanctions.
In particular, Recital 74 of the GDPR states: “the controller should be obliged to implement appropriate and effective measures and be able to demonstrate the compliance of processing activities with this Regulation, including the effectiveness of the measures (..)”
Moreover, Recital 77 of the GDPR mentions: “Guidance on the implementation of appropriate measures and on the demonstration of compliance by the controller or the processor, especially as regards the identification of the risk related to the processing, their assessment in terms of origin, nature, likelihood, and severity, and the identification of best practices to mitigate the risk could be provided in particular by means of approved codes of conduct, approved certifications, guidelines provided by the Board or indications provided by a data protection officer(…)”
KEY POINTS:
- The GDPR requires the security of every aspect of the processing of personal data. Internal and external.
- The data must be protected no matter where it goes, inside or outside the organisational boundaries.
- There is no “one size fits all” solution. The data protection solution will vary by the level of security required. A data protection impact assessment shall be carried out beforehand.
Jessica Lam
Latest posts by Jessica Lam (see all)
- Processing Personal Data - March 30, 2021
- What is Privacy? - February 25, 2021
- What is Privacy Engineering? - January 14, 2021